Enterprise network architecture stands at a transformative crossroads in 2026. As organizations accelerate cloud adoption, embrace hybrid work models, and demand performance optimization across distributed locations, the limitations of traditional connectivity solutions become increasingly apparent. While VPN technology has served remote access needs for decades, Software-Defined Wide Area Networking represents a fundamental reimagining of how enterprises connect branch offices, data centers, and cloud resources. Whether you’re a student exploring cloud-native architectures, a developer building distributed applications, or an IT leader evaluating network infrastructure investments, understanding the strategic distinctions between SD-WAN and VPN is critical for navigating the future of enterprise connectivity. This comprehensive guide examines both technologies through architectural, operational, and business lenses to help you make informed decisions that align with your organization’s digital transformation objectives.
Enterprise Networking Evolution in 2026
The enterprise WAN landscape has undergone dramatic transformation as cloud adoption, hybrid work, and digital transformation initiatives reshape connectivity requirements. By 2026, over 70% of enterprise workloads have migrated outside traditional data centers, compelling organizations to completely rearchitect their networks. The decision between SD-WAN vs VPN for Enterprise Networks now determines whether businesses merely extend legacy infrastructure or fundamentally optimize for cloud-first, distributed operations that define competitive advantage in the modern economy.
VPN: Secure Point-to-Point Connectivity
Definition
Virtual Private Network technology creates encrypted tunnels between network endpoints, enabling secure communication over public internet infrastructure. VPNs establish point-to-point or point-to-multipoint connections that protect data in transit through cryptographic protocols like IPsec, SSL/TLS, or modern alternatives including WireGuard. Traditional enterprise VPN deployments connect remote users to corporate networks or link branch offices to central data centers through dedicated tunnel configurations. Unlike their application-level proxy server counterparts, VPNs operate at the network layer providing comprehensive encryption for all traffic traversing the tunnel, making them the longstanding standard for remote access and site-to-site connectivity.
Advantages
- Proven security model: Decades of cryptographic validation with standards-based encryption protecting data confidentiality and integrity
- Simple deployment: Straightforward configuration for point-to-point connectivity with minimal infrastructure requirements
- Universal compatibility: Works with any application or protocol without requiring application-aware modifications
- Lower initial cost: Can leverage existing internet connections without specialized hardware or licensing for basic implementations
- Mature ecosystem: Extensive vendor support, troubleshooting resources, and IT workforce familiarity across industry
Disadvantages
- Performance limitations: Backhauling all traffic through central points creates latency and bandwidth bottlenecks for cloud-bound traffic
- Scalability challenges: Each new site requires individual tunnel configuration and management, increasing complexity exponentially
- No intelligent routing: Cannot dynamically select optimal paths based on application requirements or real-time network conditions
- Limited visibility: Encrypted tunnels obscure application-level traffic patterns, hindering troubleshooting and optimization
- Cloud inefficiency: Hub-and-spoke architectures force unnecessary detours for SaaS and cloud application access
Traditional VPN Deployment Models:
Remote Access VPN: Individual users connecting to corporate networks from home or travel locations through client software establishing encrypted tunnels. Site-to-Site VPN: Permanent tunnels linking branch offices to headquarters or data centers, creating virtual extensions of the private network. Furthermore, Hub-and-Spoke VPN: Central data center serves as hub with spokes connecting each branch location, forcing all inter-branch communication through the hub. Additionally, Mesh VPN: Direct tunnels between all sites enabling any-to-any communication, though configuration complexity grows quadratically with site count.
SD-WAN: Intelligent Network Fabric
Definition
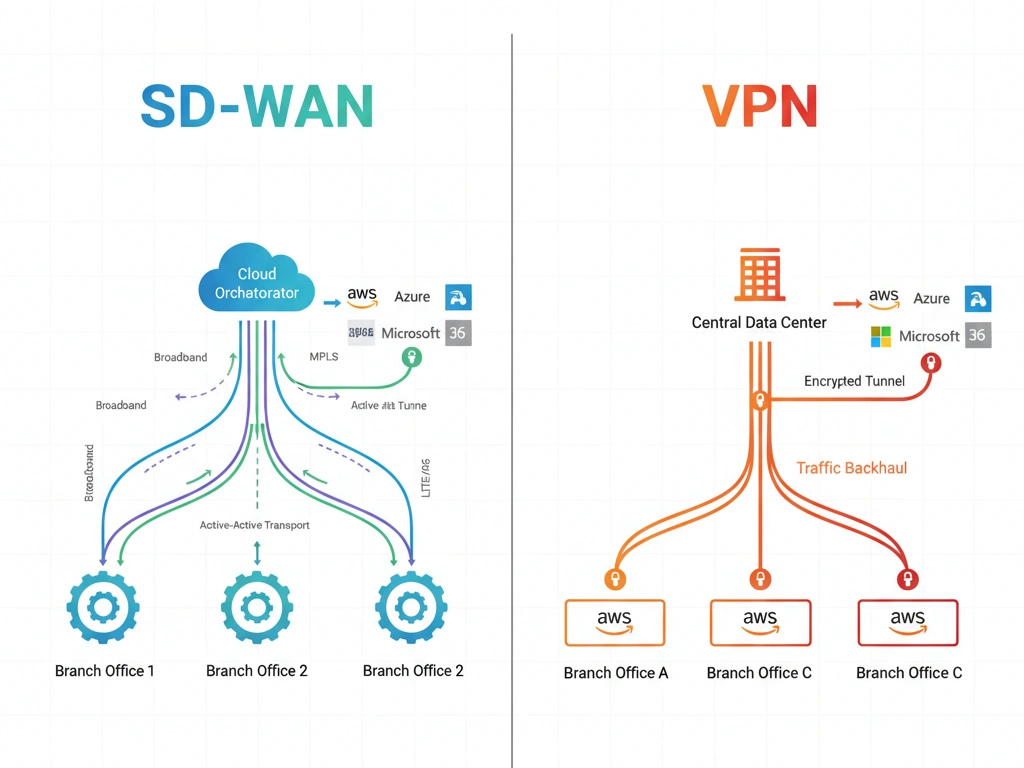
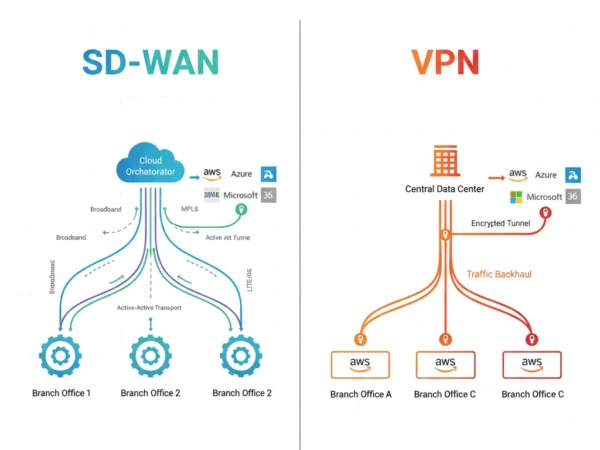
Software-Defined Wide Area Networking creates an intelligent overlay network that abstracts physical connectivity, enabling centralized control, application-aware routing, and dynamic path selection across multiple transport types. SD-WAN platforms leverage software orchestration to monitor link quality, identify applications, apply business policies, and automatically steer traffic over optimal paths whether broadband internet, MPLS circuits, LTE/5G wireless, or satellite connections. Unlike traditional VPNs that establish static tunnels, SD-WAN continuously evaluates network conditions and application requirements, dynamically adjusting routing decisions to maximize performance while maintaining security through encrypted overlays. Therefore, SD-WAN transforms the WAN from rigid infrastructure into programmable, application-centric fabric optimized for cloud-first architectures and distributed operations.
Advantages
- Application-aware routing: Identifies application types and routes traffic over paths optimized for specific performance requirements
- Multi-transport flexibility: Aggregates diverse connection types including broadband, MPLS, LTE/5G into unified fabric with automatic failover
- Cloud optimization: Enables direct internet breakout from branches to SaaS and cloud services, eliminating backhaul latency
- Centralized management: Single pane of glass for monitoring, policy enforcement, and configuration across entire WAN infrastructure
- Cost efficiency: Reduces reliance on expensive MPLS circuits by leveraging commodity broadband while maintaining QoS
- Rapid provisioning: Zero-touch deployment and automated configuration accelerate site activation from weeks to hours
Disadvantages
- Higher complexity: Sophisticated orchestration platforms require specialized expertise for optimal configuration and policy management
- Internet dependency: Performance relies heavily on underlying internet quality, which can vary significantly by geographic location
- Security integration challenges: Requires careful planning to integrate with existing security stack or migrate to SASE architecture
- Initial investment: Platform licensing, professional services, and hardware refresh create higher upfront costs than VPN solutions
- Vendor lock-in risks: Proprietary features and management platforms can create dependencies on specific vendors
SD-WAN Core Capabilities:
Dynamic Path Selection: Continuously monitors latency, jitter, packet loss, and bandwidth across all available circuits, automatically routing traffic over optimal paths. Application Classification: Deep packet inspection and machine learning identify applications in real-time, applying appropriate QoS policies and routing rules. In addition, Active-Active Transport: Utilizes multiple circuits simultaneously for throughput aggregation and instant failover without waiting for link failure detection. Moreover, Traffic Shaping: Prioritizes business-critical applications while deprioritizing or rate-limiting recreational traffic based on customizable policies. Additionally, WAN Optimization: Integrated compression, deduplication, and protocol acceleration reduce bandwidth consumption and improve application responsiveness.
Technical Architecture Analysis
VPN System Components
- VPN concentrators or gateways terminating encrypted tunnels at central locations
- Client software on endpoints for remote access or router-based tunnels for sites
- Cryptographic protocols including IPsec, SSL/TLS, WireGuard for tunnel encryption
- Authentication systems using pre-shared keys, digital certificates, or multi-factor mechanisms
- Routing tables manually configured to direct traffic through appropriate tunnels
- Network address translation for connecting disparate IP address spaces
- Split tunneling capabilities allowing selective traffic routing through VPN or direct internet
SD-WAN System Components
- Edge appliances at each location performing application identification and traffic steering
- Centralized orchestrator providing policy management, monitoring, and analytics across WAN
- Overlay network creating logical topology independent of underlying physical transport
- Application classification engines using DPI, behavioral analysis, and machine learning
- Path selection algorithms evaluating circuit quality and application SLA requirements
- Integrated security functions including next-gen firewall, IPS, and secure web gateway
- Cloud-native controllers enabling zero-touch provisioning and automated configuration updates
Network Traffic Flow Comparison
VPN Traffic Flow
- Branch office traffic enters local router or firewall configured with VPN tunnel
- All packets destined for corporate resources encrypted and encapsulated
- Traffic routes through internet to central VPN concentrator at data center
- Concentrator decrypts packets and forwards to internal network or internet
- Cloud-bound traffic backhauled through data center even if destined for nearby POP
- Return path follows same route introducing symmetric latency
- Link failure requires manual failover or routing protocol convergence
SD-WAN Traffic Flow
- Edge appliance inspects packets, classifies applications, evaluates current policies
- System measures real-time performance across all available circuits
- Traffic steered over optimal path based on application SLA requirements
- Critical apps use MPLS while general traffic leverages lower-cost broadband
- SaaS traffic breaks out directly to internet avoiding unnecessary backhaul
- Link degradation triggers automatic rerouting within milliseconds
- Orchestrator continuously adjusts policies based on network conditions and analytics
Security Architecture Differences
| Security Aspect | Traditional VPN | SD-WAN |
|---|---|---|
| Encryption | Tunnel-based encryption with IPsec, SSL/TLS, or WireGuard | Overlay encryption plus optional integration with firewall, IPS, URL filtering |
| Access Control | Network-level access after authentication, broad permissions | Application-aware policies, granular control based on user, device, location |
| Threat Protection | Requires separate firewall and security appliances at data center | Integrated next-gen firewall, IPS, malware protection at branch edge |
| Cloud Security | Forces backhaul through central security stack introducing latency | Direct internet breakout with cloud-delivered security via SASE integration |
Strategic Use Cases and Applications
When to Deploy VPN
- Remote access: Individual users connecting from home or travel locations requiring secure access to corporate resources
- Small deployments: Organizations with fewer than 5-10 locations where SD-WAN complexity exceeds benefits
- Budget constraints: Limited capital budgets preventing investment in SD-WAN platforms and professional services
- Legacy applications: Applications tightly coupled to specific network addressing or requiring predictable routing paths
- Compliance mandates: Regulatory requirements specifying particular VPN protocols or dedicated circuit isolation
When to Deploy SD-WAN
- Multi-site enterprises: Organizations with 10+ locations requiring centralized management and consistent policy enforcement
- Cloud migration: Businesses moving workloads to AWS, Azure, Google Cloud requiring optimized cloud connectivity
- SaaS adoption: Heavy usage of Microsoft 365, Salesforce, ServiceNow benefiting from direct internet breakout
- MPLS replacement: Seeking cost reduction by supplementing or replacing expensive MPLS circuits with broadband
- Application performance: Quality-sensitive applications like VoIP, video conferencing requiring dynamic path optimization
Industry-Specific Deployments
| Industry | VPN Use Cases | SD-WAN Use Cases |
|---|---|---|
| Retail | Remote corporate users accessing POS systems, seasonal workers | Connecting hundreds of stores with PCI compliance, local internet breakout for guest WiFi |
| Financial Services | Trader remote access, third-party vendor connections | Branch connectivity with guaranteed low-latency for trading platforms and customer portals |
| Healthcare | Physicians accessing EHR from home, telehealth consultations | Clinic connectivity prioritizing PACS imaging, telemedicine video, EHR synchronization |
| Manufacturing | Plant engineers remote access for troubleshooting, contractor connections | Multi-plant WAN with IoT traffic management, cloud ERP access, supply chain visibility |
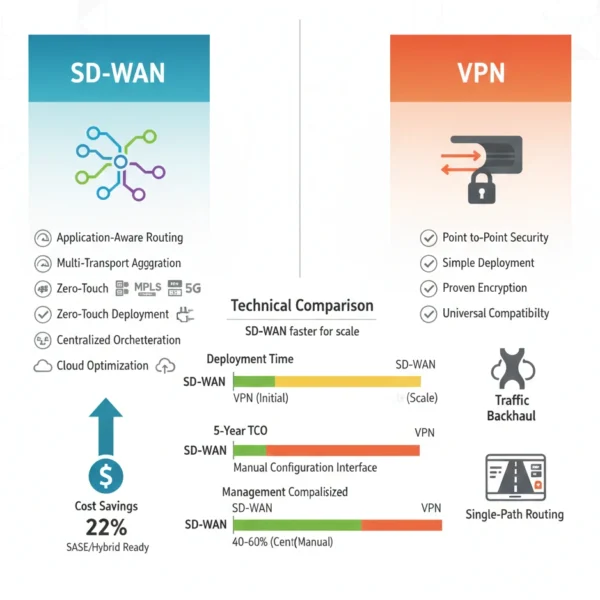
12 Critical Differences: SD-WAN vs VPN for Enterprise Networks
Aspect | VPN (Virtual Private Network) | SD-WAN (Software-Defined WAN) |
|---|---|---|
| Architecture Model | Point-to-point encrypted tunnels between specific endpoints with static routing | Intelligent overlay network with dynamic routing across multiple transport types |
| Traffic Routing | All traffic follows predetermined tunnel paths regardless of application or conditions | Application-aware routing dynamically selects optimal paths based on SLA requirements |
| Transport Flexibility | Typically relies on single transport type per tunnel, usually internet or MPLS | Aggregates multiple transports including broadband, MPLS, LTE/5G into unified fabric |
| Cloud Optimization | Forces backhaul through central hub creating latency for SaaS and cloud access | Direct local internet breakout enabling optimized paths to cloud services and SaaS |
| Management Complexity | Individual tunnel configuration and management, complexity grows quadratically with sites | Centralized orchestration with single pane of glass for policy management across WAN |
| Performance Visibility | Limited visibility into application performance, encrypted tunnels obscure traffic patterns | Deep application analytics with real-time monitoring of QoS metrics per application |
| Failover Capabilities | Manual failover or routing protocol convergence taking seconds to minutes | Sub-second automatic failover with active-active transport utilization |
| Quality of Service | Basic QoS limited by tunnel capacity, no application-level prioritization | Application-aware QoS with dynamic bandwidth allocation based on business policies |
| Deployment Speed | Manual configuration per site, typically weeks for provisioning and testing | Zero-touch deployment with automated provisioning, hours to activate new sites |
| Cost Structure | Lower initial costs but hidden expenses in bandwidth waste and operational overhead | Higher upfront investment offset by MPLS reduction and operational efficiency gains |
| Security Integration | Separate security appliances required, centralized inspection creates bottlenecks | Integrated security functions or seamless SASE integration with cloud-delivered security |
| Scalability Model | Linear growth in complexity and management burden as sites increase | Horizontal scaling with consistent management overhead regardless of site count |
Implementation Strategy and Migration Planning
Technology Selection Decision Tree
- Assess Current State: First, inventory existing WAN infrastructure including circuit types, locations, applications, and current pain points around performance or cost.
- Define Requirements: Then, document specific business needs including cloud usage, application criticality, branch count, growth projections, and budget constraints.
- Evaluate Network Architecture: Additionally, determine if hub-and-spoke model causing cloud access bottlenecks or if direct internet breakout would benefit SaaS performance.
- Calculate Financial Impact: Furthermore, model total cost of ownership over 3-5 years including capital expenses, operational costs, and opportunity costs of poor performance.
- Consider Security Posture: Subsequently, assess whether centralized security inspection model aligns with zero-trust principles or SASE architecture goals.
- Plan Migration Approach: Finally, determine phased rollout strategy balancing risk mitigation with urgency to capture benefits from modernization.
VPN to SD-WAN Migration Roadmap
Phase 1: Foundation (Months 1-2)
- Select SD-WAN vendor and deployment model (managed vs DIY)
- Design WAN topology and policy framework
- Identify pilot sites representing diverse scenarios
- Procure circuits and equipment for initial rollout
- Establish baseline performance metrics for comparison
Phase 2: Pilot (Months 3-4)
- Deploy SD-WAN at 2-3 pilot locations running parallel to VPN
- Validate application performance and user experience
- Tune policies based on observed traffic patterns
- Train IT staff on management platform and operations
- Document lessons learned and refine rollout plan
Phase 3: Scale (Months 5-12)
- Roll out SD-WAN to remaining sites in waves
- Gradually decommission VPN tunnels as SD-WAN stabilizes
- Optimize MPLS footprint replacing with broadband where appropriate
- Implement advanced features like cloud on-ramps and SASE integration
- Establish ongoing optimization and governance processes
Implementation Best Practices
Critical Success Factors
- Start with clear business objectives beyond technology refresh, measuring against tangible KPIs
- Maintain hybrid approach during transition keeping VPN as backup until SD-WAN proves stable
- Invest heavily in Day 2 operations planning including monitoring, troubleshooting, and change management
- Choose vendors with strong professional services and responsive support for complex deployments
- Implement application classification carefully ensuring business-critical apps properly identified
- Plan security architecture thoughtfully integrating with existing tools or migrating to SASE model
Common Migration Pitfalls
- Never rush pilot phase, premature scaling amplifies configuration errors across entire network
- Avoid underestimating internet circuit requirements, broadband quality varies significantly by location
- Don’t neglect last-mile redundancy planning, single circuit dependency negates SD-WAN benefits
- Resist temptation to eliminate all MPLS immediately, some applications genuinely require dedicated bandwidth
- Never deploy without comprehensive monitoring, visibility loss during migration creates operational blindness
- Don’t ignore organizational change management, user and IT staff training critical for successful adoption
Cost Analysis and ROI Comparison
Initial Investment
VPN: $500-$2,000 per site for equipment and setup
SD-WAN: $15,000-$50,000 for platform licensing plus $2,000-$5,000 per site
Monthly Recurring
VPN: Circuit costs plus 10-15% for management
SD-WAN: 30-50% reduction in circuit costs through MPLS replacement
Break-Even Timeline
VPN: Immediate, lower upfront cost
SD-WAN: 18-36 months depending on MPLS savings and site count
Five-Year Total Cost of Ownership
| Cost Component | VPN (50 Sites) | SD-WAN (50 Sites) | SD-WAN Advantage |
|---|---|---|---|
| Initial Deployment | $100,000 | $350,000 | -$250,000 |
| Circuit Costs (5 years) | $3,000,000 | $1,800,000 | +$1,200,000 |
| Platform/Licensing | $50,000 | $500,000 | -$450,000 |
| Operational Labor | $750,000 | $400,000 | +$350,000 |
| Total 5-Year TCO | $3,900,000 | $3,050,000 | +$850,000 (22% savings) |
While SD-WAN requires substantially higher upfront investment, enterprises with 20+ sites typically achieve 20-40% total cost of ownership reduction over five years through MPLS circuit elimination and operational efficiency gains. Organizations with fewer than 10 sites may find VPN more economical unless cloud performance issues create quantifiable business impact. The break-even point depends heavily on existing MPLS spend, with MPLS-heavy networks recouping SD-WAN investment faster through aggressive circuit replacement strategies.
Quantifiable Business Benefits Beyond Cost
VPN Business Impact
- User Productivity: VPN latency costs knowledge workers 30-60 minutes daily in cloud app delays
- Deployment Speed: New site activation requires 4-8 weeks from circuit order to production
- Network Availability: Manual failover results in 15-30 minute outages during circuit failures
- IT Efficiency: Troubleshooting consumes 20-30 hours monthly due to limited visibility
SD-WAN Business Impact
- User Productivity: 40-60% improvement in cloud application response times boosting efficiency
- Deployment Speed: Zero-touch provisioning enables site activation in 24-48 hours
- Network Availability: Sub-second failover maintains 99.95%+ uptime during circuit issues
- IT Efficiency: Centralized management reduces troubleshooting time by 50-70%
Hybrid Deployment and SASE Architecture
The Hybrid Reality: SD-WAN Plus VPN
Rather than complete replacement, most enterprises in 2026 deploy SD-WAN for site-to-site connectivity while maintaining VPN for remote user access and specific use cases. This hybrid approach leverages each technology’s strengths while mitigating weaknesses. SD-WAN connects branch offices with intelligent routing and centralized management, while VPN provides simple, secure remote access for mobile workforce. Consequently, the question transforms from SD-WAN versus VPN into SD-WAN plus VPN optimized for specific workloads.
Optimal Hybrid Architecture Pattern
SD-WAN Workloads
- Branch-to-branch communication benefiting from direct mesh connectivity
- Branch-to-cloud traffic requiring application-aware routing and local breakout
- Branch-to-data center access for on-premises applications and shared services
- IoT and operational technology traffic requiring specialized QoS policies
- High-bandwidth applications like video conferencing, file transfers, backup replication
VPN Workloads
- Remote employee access from home offices, hotels, airports, coffee shops
- Contractor and vendor connectivity requiring temporary, limited-scope access
- Mobile device access for smartphones and tablets used by field personnel
- Disaster recovery scenarios where SD-WAN infrastructure unavailable
- Legacy applications incompatible with SD-WAN routing behaviors or addressing
SASE: The Convergence of SD-WAN and Security
Understanding SASE Architecture
Secure Access Service Edge represents the next evolution beyond traditional SD-WAN by converging networking and security into unified cloud-delivered service. By 2026, over 60% of SD-WAN deployments have integrated SASE capabilities compared to 35% in 2020, driven by distributed workforce, cloud adoption, and zero-trust security mandates.
SASE Core Components:
- SD-WAN Foundation: Intelligent overlay providing optimized connectivity across sites, users, and cloud resources
- Zero Trust Network Access: Identity-based access control replacing VPN with granular, application-level permissions
- Secure Web Gateway: Cloud-delivered URL filtering, malware protection, data loss prevention for internet traffic
- Cloud Access Security Broker: Visibility and control for SaaS applications with shadow IT detection and DLP
- Firewall as a Service: Next-generation firewall capabilities delivered from cloud POPs nearest to users
Migration Strategy: Organizations typically start with SD-WAN for site connectivity, then progressively integrate security services as vendor capabilities mature and internal expertise develops. Complete SASE transformation typically requires 24-36 months including organizational change management beyond pure technology deployment.
VPN Role in SASE Context
Traditional VPN Limitations
- Provides network-level access contradicting zero-trust principles
- Forces traffic hairpinning through data center degrading cloud performance
- Lacks application-level visibility and control critical for modern security
- Struggles scaling to support thousands of remote workers efficiently
- Creates poor user experience with frequent disconnects and authentication prompts
ZTNA Alternative Benefits
- Grants access to specific applications not entire network reducing attack surface
- Routes users to closest cloud POP minimizing latency for SaaS and cloud apps
- Enforces granular policies based on user, device, location, and risk posture
- Scales elastically in cloud accommodating workforce fluctuations seamlessly
- Delivers seamless user experience with persistent connectivity and adaptive authentication
Frequently Asked Questions: SD-WAN vs VPN for Enterprise Networks
Making Strategic Networking Decisions in 2026
The decision between SD-WAN vs VPN for Enterprise Networks transcends simple technology selection, representing strategic choice about organizational agility, cloud readiness, and operational efficiency. Both technologies deliver critical connectivity capabilities when deployed appropriately, and their optimal combination varies based on specific business requirements, existing infrastructure, and transformation timeline.
Deploy VPN When:
- Connecting remote users from diverse locations without fixed infrastructure
- Managing fewer than 10 sites where SD-WAN complexity outweighs benefits
- Operating with limited capital budgets preventing SD-WAN investment
- Supporting temporary connectivity needs for projects or contractors
- Maintaining disaster recovery access paths as SD-WAN backup
- Working with legacy applications incompatible with SD-WAN routing
Deploy SD-WAN When:
- Operating 20+ distributed sites requiring centralized management
- Migrating significant workloads to cloud platforms or SaaS applications
- Spending heavily on MPLS circuits creating cost reduction opportunity
- Experiencing cloud application performance issues from backhaul latency
- Planning rapid expansion requiring fast new site activation
- Pursuing SASE architecture aligning networking with security transformation
Strategic Recommendation for 2026:
Most enterprises benefit from hybrid approach deploying SD-WAN for site-to-site connectivity while maintaining VPN for remote user access and specific edge cases. Begin transformation by assessing current WAN pain points, particularly around cloud performance and MPLS costs. Pilot SD-WAN at 2-3 representative locations proving value before full commitment. Maintain parallel VPN infrastructure during transition as insurance against unforeseen issues. Plan 18-36 month migration timeline allowing thorough testing, staff training, and organizational adaptation. Consider managed SD-WAN services if internal expertise limited or IT resources constrained. Finally, evaluate SASE roadmap determining whether integrated security capabilities justify platform selection even if not immediately deployed. Organizations executing thoughtful migrations rather than rushed implementations achieve superior outcomes with lower risk and faster value realization.
The networking landscape in 2026 rewards organizations understanding these technologies as complementary capabilities optimized for different connectivity patterns. Whether you’re a student exploring cloud-native architectures, a developer building distributed applications, or an IT leader architecting enterprise infrastructure, recognizing when to apply point-to-point VPN tunnels versus intelligent SD-WAN fabric determines your success navigating the cloud-first, distributed future. Your competitive advantage comes not from technology brand selection but from strategic deployment aligning networking capabilities with business objectives, user requirements, and operational realities. Just as VPN and proxy servers serve distinct networking needs, SD-WAN and VPN each provide unique value when applied to appropriate use cases within comprehensive enterprise architecture.
Related Topics Worth Exploring
SASE Architecture Deep Dive
Explore how Secure Access Service Edge converges networking and security into unified cloud-delivered framework transforming enterprise connectivity.
Zero Trust Network Access
Learn how ZTNA replaces traditional VPN with identity-based, application-level access control aligned with modern security principles.
Cloud Networking Fundamentals
Discover best practices for connecting distributed enterprises to AWS, Azure, and Google Cloud with optimized performance and security.