In today’s enterprise IT landscape, network security and privacy have become non-negotiable requirements. Whether you’re a student learning about networking fundamentals, a developer building distributed systems, or an IT professional managing corporate infrastructure, understanding the difference between VPN services and proxy servers is crucial for making informed decisions about your network architecture. Both technologies route traffic through intermediary servers and can mask IP addresses, but they operate fundamentally differently and serve distinct use cases. This comprehensive guide examines both solutions from technical, security, and operational perspectives to help you choose the right tool for your specific requirements.
Understanding Network Privacy Fundamentals in 2026
Network privacy and security technologies have evolved significantly to meet the demands of distributed workforces, cloud infrastructure, and increasing cyber threats. While both proxy servers and VPN services provide ways to route traffic through intermediary systems, the choice between VPN Services vs Proxy Servers for IT Networks now determines your organization’s security posture, compliance readiness, and operational efficiency.
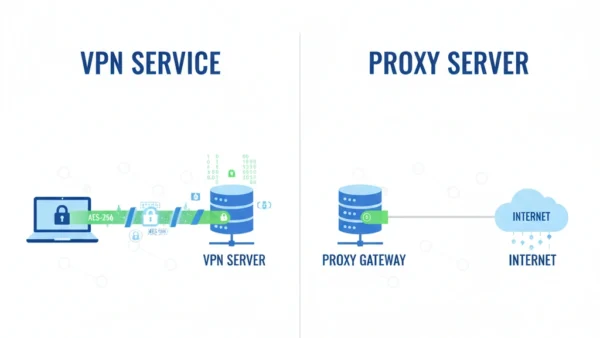
Proxy Servers: Application-Level Traffic Routing
Definition
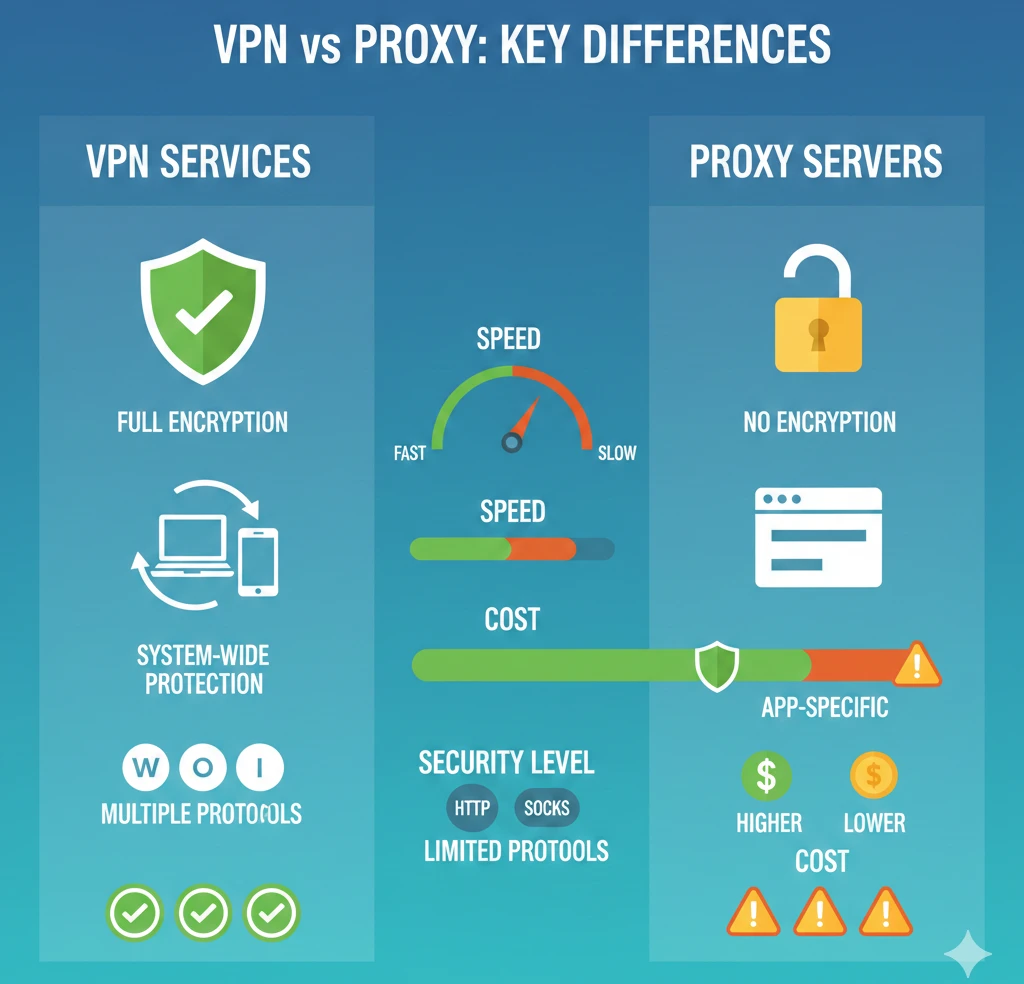
A proxy server is an intermediary server that sits between client applications and the internet, forwarding requests on behalf of users. When you configure a proxy, your application sends requests to the proxy server, which then retrieves content from the destination and returns it to you. The destination server sees the proxy’s IP address rather than yours. Unlike VPN services, proxies typically operate at the application layer and handle specific protocols without encrypting the connection.
Advantages
- Faster performance: No encryption overhead means lower latency and higher throughput for simple tasks
- Application-specific control: Configure different proxies for different applications or browser instances
- Content caching: Frequently accessed content can be cached locally, reducing bandwidth and improving speed
- Lower resource usage: Minimal CPU and memory requirements compared to VPN encryption processes
Disadvantages
- No encryption: Traffic between your device and the proxy server travels in plaintext, exposing data to interception
- Limited scope: Only protects traffic from configured applications, leaving other network activity exposed
- Security risks: Many free proxies log data, inject ads, or even distribute malware to users
- Protocol restrictions: HTTP proxies only handle web traffic, requiring different proxy types for other protocols
Common Proxy Types:
HTTP Proxies: Handle standard web browsing traffic and are widely supported in browsers and applications. HTTPS Proxies: Forward encrypted HTTPS connections but don’t add encryption themselves. Furthermore, SOCKS5 Proxies: Protocol-agnostic proxies that can handle any type of traffic including FTP, SMTP, and P2P connections. Additionally, Transparent Proxies: Intercept traffic without requiring client configuration, commonly used for content filtering in corporate networks.
VPN Services: Comprehensive Network Security
Definition
A Virtual Private Network service creates an encrypted tunnel between your device and a remote VPN server, protecting all network traffic that passes through it. VPNs operate at the network layer, encrypting everything from web browsing to email, file transfers, and application data. When connected to a VPN, your device establishes a secure connection using protocols like WireGuard or OpenVPN, ensuring that even your internet service provider cannot see what you’re doing online. Therefore, VPNs provide comprehensive protection for all internet activity.
Advantages
- Full encryption: Military-grade encryption protects all data in transit from your device to the VPN server
- System-wide protection: Covers all applications and network connections automatically without individual configuration
- Advanced security features: DNS leak protection, kill switches, and split tunneling enhance privacy and control
- Remote access capabilities: Securely connect to corporate networks from anywhere, enabling distributed workforces
Disadvantages
- Performance overhead: Encryption and decryption processes can reduce connection speeds, especially with older protocols
- Higher costs: Quality VPN services require subscription fees, and enterprise solutions demand significant infrastructure investment
- Configuration complexity: Enterprise VPN deployments require careful planning, certificate management, and ongoing maintenance
- Potential blocking: Some services and countries actively detect and block VPN traffic using deep packet inspection
Modern VPN Protocols:
WireGuard: Modern lightweight protocol offering exceptional speed with lean codebase, ideal for mobile devices and high-performance needs. OpenVPN: Industry-standard open-source protocol with proven reliability, extensive auditing, and broad platform support. In addition, IKEv2/IPSec: Built into many operating systems, excels at maintaining connections when switching between networks. Moreover, NordWhisper: Emerging protocol designed to bypass censorship by mimicking normal web traffic patterns.
Technical Architecture Deep Dive
Proxy Server Components
- Application-layer gateway operating at OSI Layer 7
- Protocol-specific handlers for HTTP, HTTPS, SOCKS, or FTP
- Optional caching engines for frequently accessed content
- Access control lists and filtering rules for content moderation
- Logging systems that track user requests and bandwidth usage
- Load balancing capabilities for distributing traffic across multiple proxy nodes
VPN Service Components
- Network-layer encryption operating at OSI Layer 3 or 4
- Tunneling protocols like WireGuard, OpenVPN, or IKEv2/IPSec
- Certificate infrastructure for authentication and key exchange
- Encryption algorithms including AES-256 or ChaCha20-Poly1305
- DNS servers to prevent leaks and maintain privacy
- Kill switch mechanisms that block traffic if VPN connection drops
Network Traffic Flow Comparison
Proxy Traffic Flow
- Application sends request to proxy server address
- Proxy receives unencrypted request with destination URL
- Proxy forwards request to destination server using its own IP
- Destination server responds to proxy server
- Proxy returns response to client application
- Other applications bypass proxy entirely unless configured
VPN Traffic Flow
- VPN client encrypts all outgoing network packets
- Encrypted packets are wrapped in VPN protocol headers
- Tunnel transports encrypted data to VPN server
- VPN server decrypts packets and forwards to destination
- Return traffic is encrypted by VPN server
- Client receives and decrypts packets automatically for all applications
Real-World Applications and Use Cases
When to Use Proxy Servers
- Web scraping operations: Rotate IP addresses to avoid rate limiting and distribute requests across multiple sources
- Content filtering: Corporate networks implementing acceptable use policies and blocking malicious websites
- Geographic testing: Developers testing how applications behave from different regional locations
- Bandwidth optimization: Caching frequently accessed resources to reduce external bandwidth consumption
- Load distribution: Reverse proxies balancing traffic across multiple backend servers
When to Use VPN Services
- Remote workforce access: Employees securely connecting to corporate networks from home or while traveling
- Public WiFi protection: Encrypting all traffic when using untrusted networks in cafes, airports, or hotels
- Site-to-site connections: Linking multiple office locations through encrypted tunnels over the internet
- Compliance requirements: Meeting regulatory mandates for data protection in healthcare, finance, or government sectors
- Privacy-focused browsing: Preventing ISPs, governments, or third parties from monitoring online activities
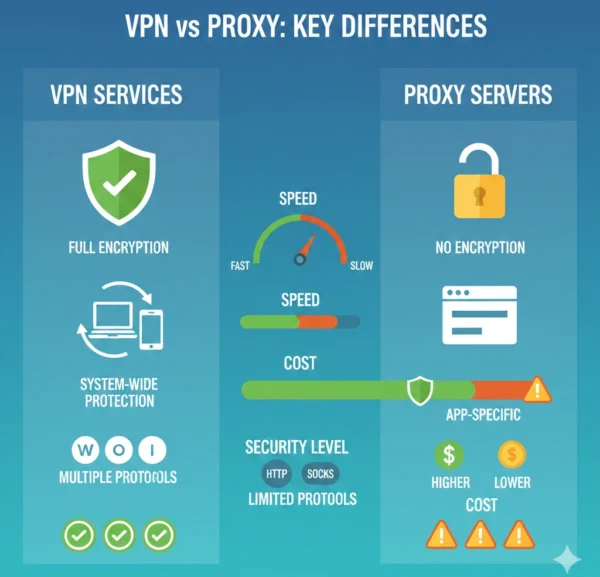
10 Critical Differences: VPN Services vs Proxy Servers
Aspect | Proxy Servers | VPN Services |
|---|---|---|
| Encryption | No encryption between client and proxy server, traffic visible to ISPs and network monitors | End-to-end encryption using AES-256 or ChaCha20, making traffic unreadable to third parties |
| Scope of Protection | Only protects traffic from specifically configured applications like web browsers | Protects all network traffic system-wide including background applications and services |
| Network Layer | Operates at application layer handling specific protocols like HTTP or SOCKS | Operates at network layer encrypting all IP packets regardless of protocol |
| Setup Complexity | Simple configuration in browser settings or application preferences | Requires client software installation and authentication with certificates or credentials |
| Performance Impact | Minimal overhead, often faster due to caching and no encryption processing | Moderate overhead from encryption, though modern protocols like WireGuard minimize impact |
| Privacy Protection | Hides IP from destination but not from ISP, proxy provider can see all activity | Hides activity from ISP and destination, only VPN provider can potentially log traffic |
| Protocol Support | Limited to specific protocols, HTTP proxies can’t handle non-web traffic | Supports all protocols transparently including HTTP, FTP, SSH, gaming, VoIP |
| Authentication | Optional username/password, often no authentication for public proxies | Strong authentication required using certificates, pre-shared keys, or multi-factor methods |
| Security Features | Basic IP masking and content filtering, no built-in leak protection | DNS leak protection, kill switches, split tunneling, and advanced security controls |
| Enterprise Adoption | Used for web filtering, content caching, and reverse proxy load balancing | Standard for remote access, site-to-site connectivity, and zero-trust architectures |
Implementation Best Practices
Configuration Examples
Proxy Server Configuration (SOCKS5)
# Configure SOCKS5 proxy in Python application
import requests
from requests.auth import HTTPProxyAuth
proxies = {
'http': 'socks5://username:password@proxy.company.com:1080',
'https': 'socks5://username:password@proxy.company.com:1080'
}
# Application-specific request
response = requests.get(
'https://api.example.com/data',
proxies=proxies,
timeout=30
)
# Other applications not using proxy remain unprotected
print(response.json())VPN Configuration (WireGuard)
# WireGuard configuration file /etc/wireguard/wg0.conf
[Interface]
PrivateKey = YOUR_PRIVATE_KEY
Address = 10.0.0.2/24
DNS = 1.1.1.1
[Peer]
PublicKey = SERVER_PUBLIC_KEY
Endpoint = vpn.company.com:51820
AllowedIPs = 0.0.0.0/0
PersistentKeepalive = 25
# Activate VPN connection
# wg-quick up wg0
# All system traffic now encrypted and routed through VPN
Decision Framework for IT Networks
- Assess Security Requirements: First, determine whether you need encryption, compliance with regulations like HIPAA or GDPR, and protection against eavesdropping.
- Evaluate Network Scope: Then, identify whether protection is needed for specific applications or comprehensive system-wide coverage.
- Analyze Performance Needs: Additionally, measure acceptable latency, bandwidth requirements, and whether caching benefits outweigh encryption overhead.
- Consider Deployment Scale: Furthermore, plan for number of concurrent users, geographic distribution, and high availability requirements.
- Review Budget Constraints: Subsequently, calculate total cost of ownership including infrastructure, licensing, and ongoing operational expenses.
- Plan for Management: Finally, ensure your team has expertise for ongoing monitoring, certificate management, and troubleshooting of chosen solution.
Security Best Practices
Recommended Practices
- Use VPNs for remote access and sensitive communications
- Deploy proxies for content filtering and web traffic management
- Implement certificate pinning to prevent man-in-the-middle attacks
- Enable DNS leak protection on all VPN connections
- Regularly audit proxy and VPN logs for suspicious activity
- Use WireGuard or OpenVPN protocols for production VPN deployments
Common Mistakes to Avoid
- Never use free public proxies for sensitive corporate data
- Avoid relying on proxies alone for security in hostile networks
- Don’t trust VPN providers without independent security audits
- Never disable certificate validation to bypass warnings
- Avoid deprecated protocols like PPTP or outdated SOCKS4
- Don’t assume proxy or VPN alone satisfies compliance requirements
Cost and Performance Comparison
Initial Setup Costs
Proxy Servers: $500-$5,000 for enterprise solutions
VPN Services: $10,000-$50,000 for infrastructure and licensing
Per-User Monthly Cost
Proxy Servers: $2-$10 per user for commercial services
VPN Services: $5-$15 per user for business plans
Performance Impact
Proxy Servers: 5-15% overhead with caching benefits
VPN Services: 10-30% overhead depending on protocol and distance
Performance Benchmarks (2026 Data)
| Metric | HTTP Proxy | SOCKS5 Proxy | WireGuard VPN | OpenVPN |
|---|---|---|---|---|
| Connection Latency | 5-20ms | 10-25ms | 15-30ms | 25-50ms |
| Throughput (1Gbps Link) | 950 Mbps | 920 Mbps | 850 Mbps | 650 Mbps |
| CPU Usage (per connection) | Low | Low | Medium | High |
| Mobile Battery Impact | Minimal | Minimal | Low | Moderate |
While proxy servers offer superior performance for specific applications, VPN services provide comprehensive security that justifies the performance overhead. Modern protocols like WireGuard have significantly narrowed the performance gap, making VPNs viable even for bandwidth-intensive operations. Organizations should prioritize security requirements over raw performance unless operating in controlled, trusted environments where encryption is unnecessary.
Security and Compliance Considerations
Critical Security Warning
Proxy servers transmit data in plaintext between your device and the proxy, making them vulnerable to interception on untrusted networks. Never use proxies for transmitting passwords, financial data, or personally identifiable information over public WiFi or hostile networks. VPN encryption is essential for these scenarios.
Regulatory Compliance Matrix
| Compliance Framework | Proxy Server Suitability | VPN Service Requirements |
|---|---|---|
| GDPR (EU Data Protection) | Insufficient alone, no encryption for data in transit | Meets requirements when combined with proper logging controls |
| HIPAA (Healthcare) | Does not satisfy encryption requirements for ePHI | Approved when using FIPS 140-2 validated encryption |
| PCI DSS (Payment Cards) | Cannot protect cardholder data transmission | Required for remote access to cardholder data environments |
| SOC 2 Type II | May satisfy availability controls for content delivery | Essential for security and confidentiality control objectives |
| NIST Cybersecurity Framework | Supports “Detect” and “Respond” functions via logging | Critical for “Protect” function with encryption requirements |
Hybrid Architecture Approach
Layered Security Strategy
Many organizations deploy both technologies strategically to maximize benefits while controlling costs. A recommended architecture includes:
- VPN for remote workforce accessing corporate resources
- Forward proxy for outbound web traffic filtering and monitoring
- Reverse proxy for load balancing and protecting web applications
- VPN for site-to-site connectivity between office locations
- SOCKS5 proxy for specific development and testing workflows
Zero Trust Network Access (ZTNA)
The future of network security moves beyond traditional VPN perimeters to zero trust models where:
- Every connection is authenticated and encrypted regardless of source
- Users receive least-privilege access to specific applications only
- Continuous verification replaces implicit trust from network location
- Micro-segmentation prevents lateral movement in breaches
- Identity-based policies supersede IP address-based controls
Frequently Asked Questions: VPN Services vs Proxy Servers for IT Networks
Making the Strategic Choice for Your IT Network in 2026
The decision between VPN Services vs Proxy Servers for IT Networks depends entirely on your specific security requirements, use cases, and operational constraints. Both technologies serve important but distinct purposes in modern network architecture, and understanding their appropriate applications is crucial for building secure, efficient infrastructure.
Choose Proxy Servers When:
- You need application-specific traffic routing without encryption
- Content caching and bandwidth optimization are priorities
- Web filtering and acceptable use policies must be enforced
- Maximum performance is critical and security isn’t compromised
- Load balancing web traffic across multiple backend servers
- Development teams need geographic location testing capabilities
Choose VPN Services When:
- Comprehensive encryption is required for all network traffic
- Remote workers need secure access to corporate resources
- Compliance mandates encryption for data in transit
- Users connect from untrusted networks like public WiFi
- Privacy from ISPs and network monitors is important
- Site-to-site connectivity between offices is needed
Best Practice Recommendation:
Most modern IT environments benefit from deploying both technologies strategically rather than choosing one over the other. Use VPN services for remote access, encrypted communications, and protecting mobile users on untrusted networks. Deploy proxy servers for web content filtering, caching frequently accessed resources, and application-specific traffic management. This layered approach provides defense in depth, optimizes performance where appropriate, and ensures security where necessary. Furthermore, consider emerging zero trust network access models that combine the best aspects of both technologies with identity-based controls and continuous verification.
As network security continues to evolve in 2026, the most successful organizations understand that proxy servers and VPN services are complementary tools in a comprehensive security strategy. Your competitive advantage comes from deploying each technology where it provides maximum value while building the infrastructure and expertise to manage both effectively. Whether you’re a student learning these concepts, a developer building networked applications, or an IT professional architecting enterprise systems, understanding these distinctions enables you to make informed decisions that balance security, performance, and cost.
Related Topics Worth Exploring
Zero Trust Network Architecture
Learn how modern security models verify every connection regardless of source, moving beyond traditional perimeter-based defenses.
WireGuard Protocol Deep Dive
Explore the technical architecture, cryptographic primitives, and performance characteristics of the fastest modern VPN protocol.
Enterprise Network Security
Discover comprehensive strategies for protecting corporate networks including firewalls, intrusion detection, and security information event management.